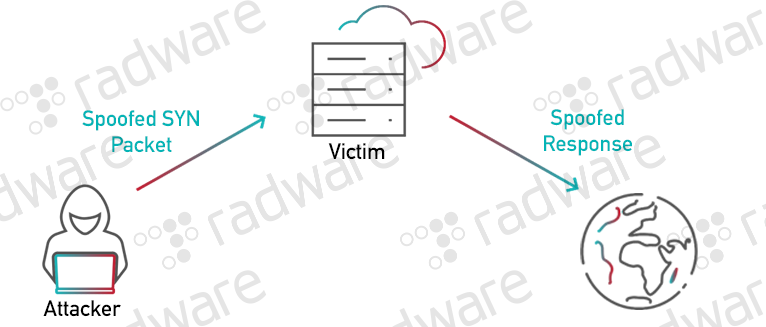
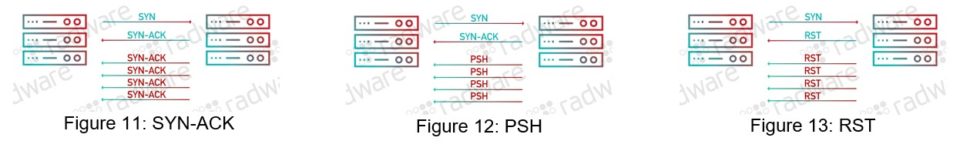
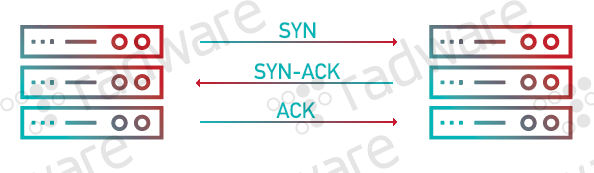
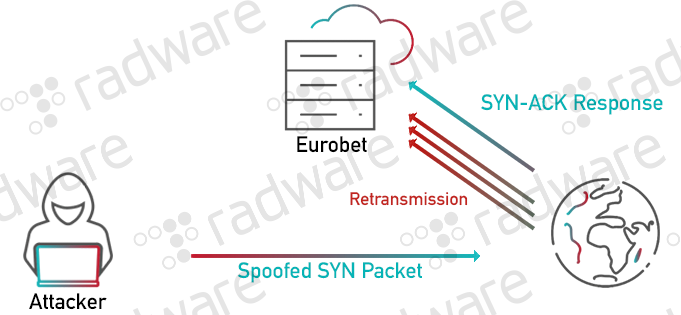
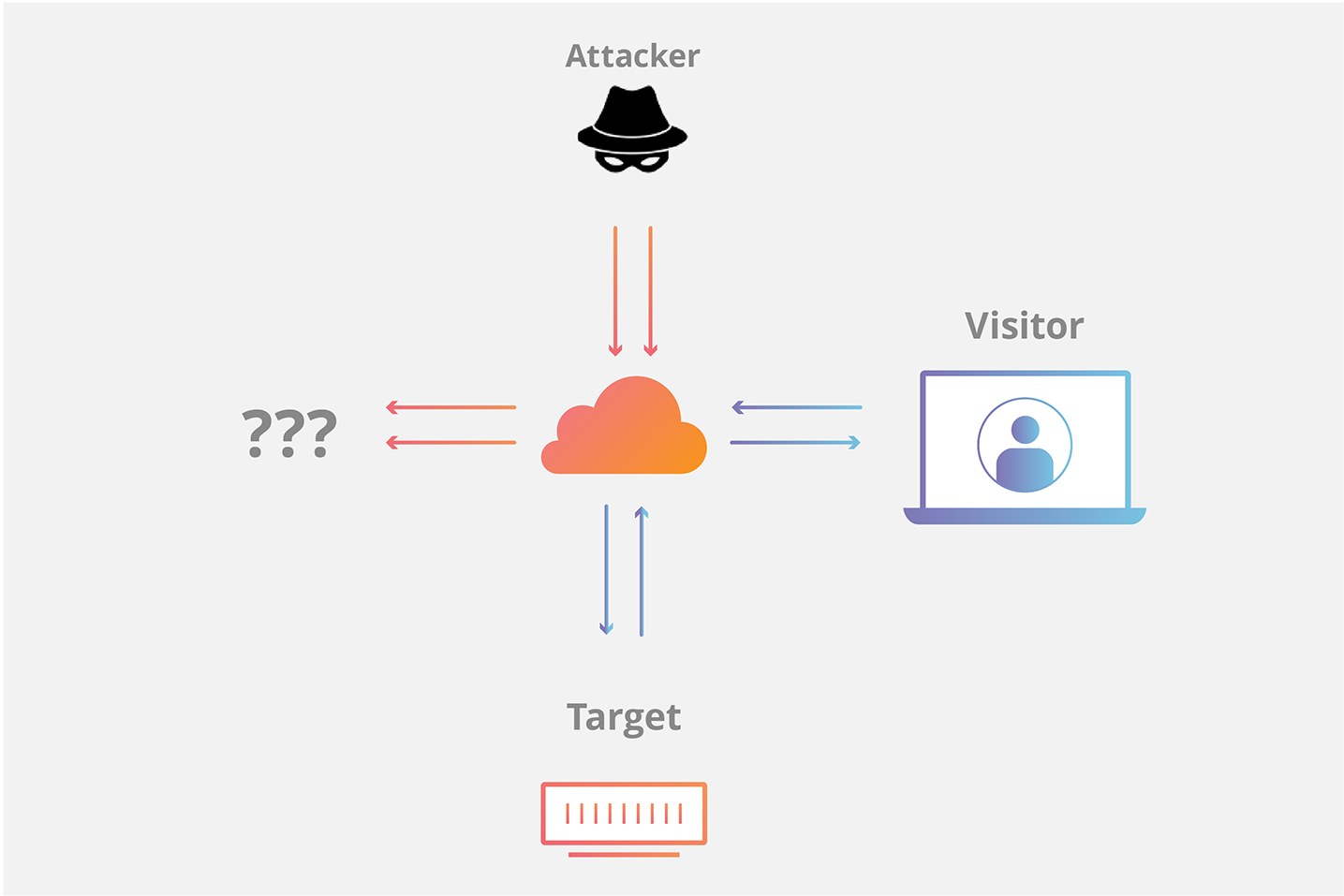
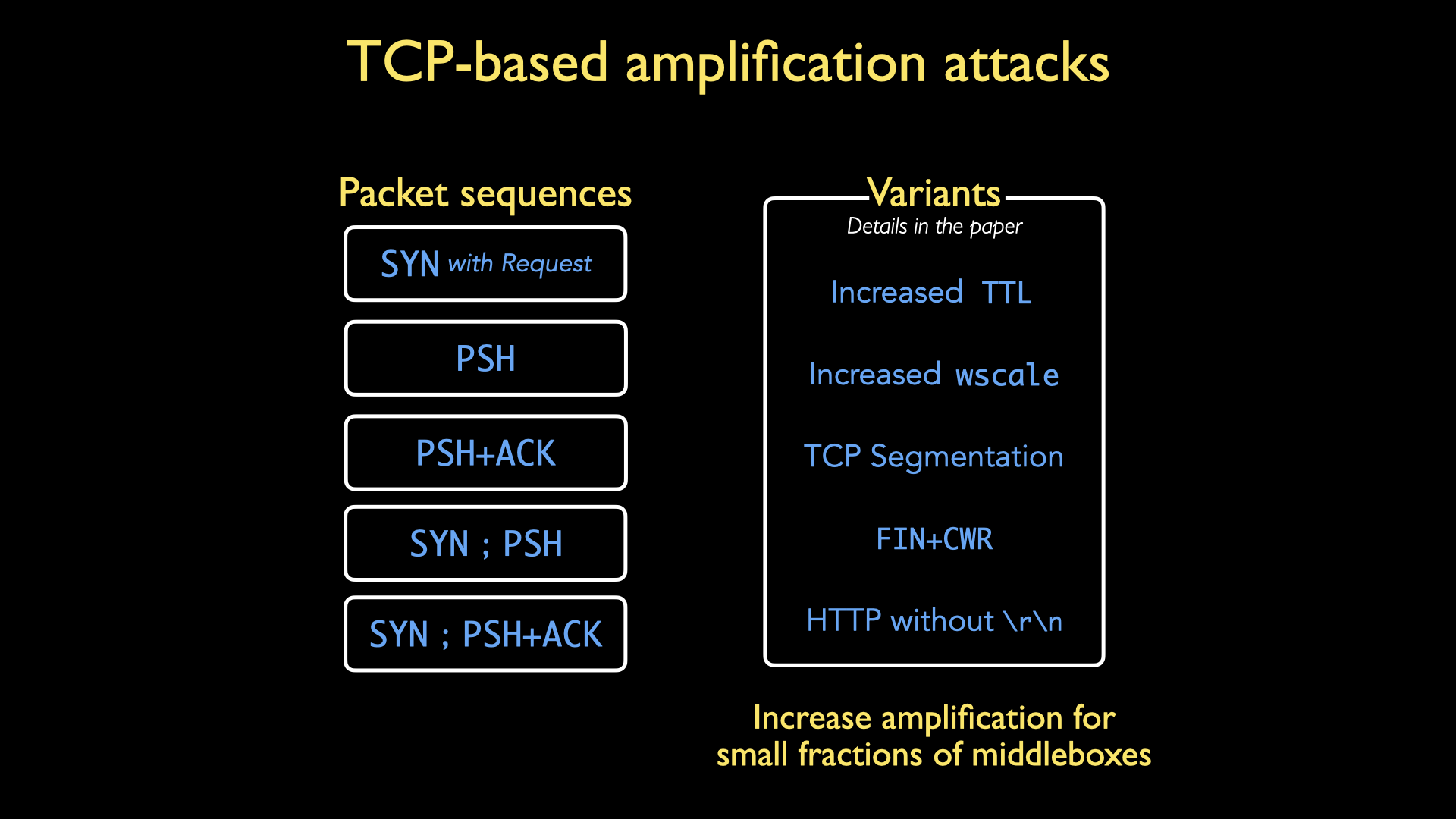
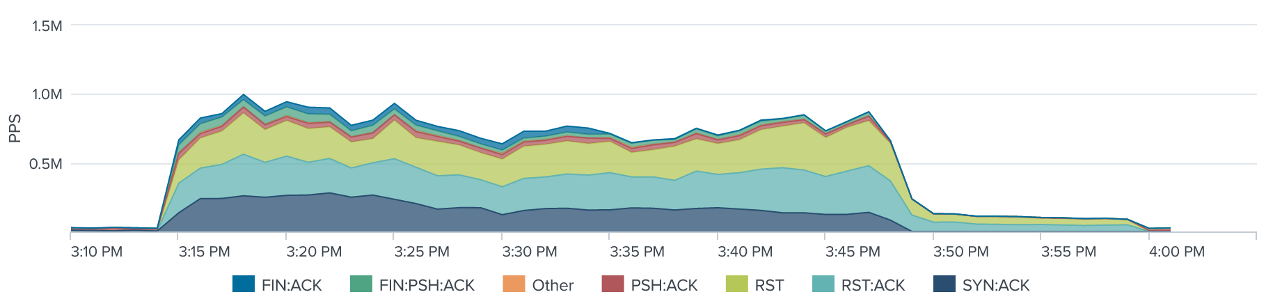
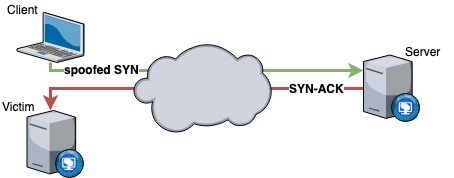
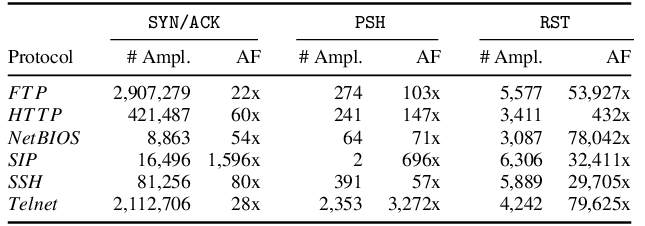
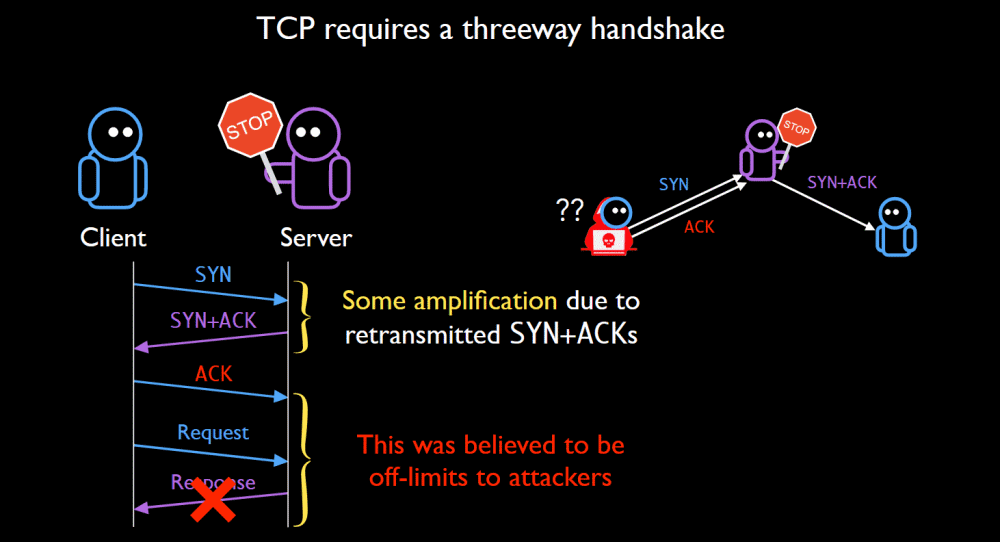
Principles and Characteristics of TCP Reflection Attacks - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Principles and Characteristics of TCP Reflection Attacks - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Research and Analysis of Middlebox-based TCP Reflective Amplification Attacks - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.